Instant Validation, Instant Action Items
Built for the DoD Cyber Workforce
We speak your language. Native support for 8140/NICE Framework. Hands-free policy updates, integrations with manpower databases, and CAC-enabled access.
Mission-Ready & As Dynamic As Your Team
Deployable in classified environments. Built to FedRAMP High standards. Ready for your toughest requirements.
Workforce Readiness at Cyber Speed

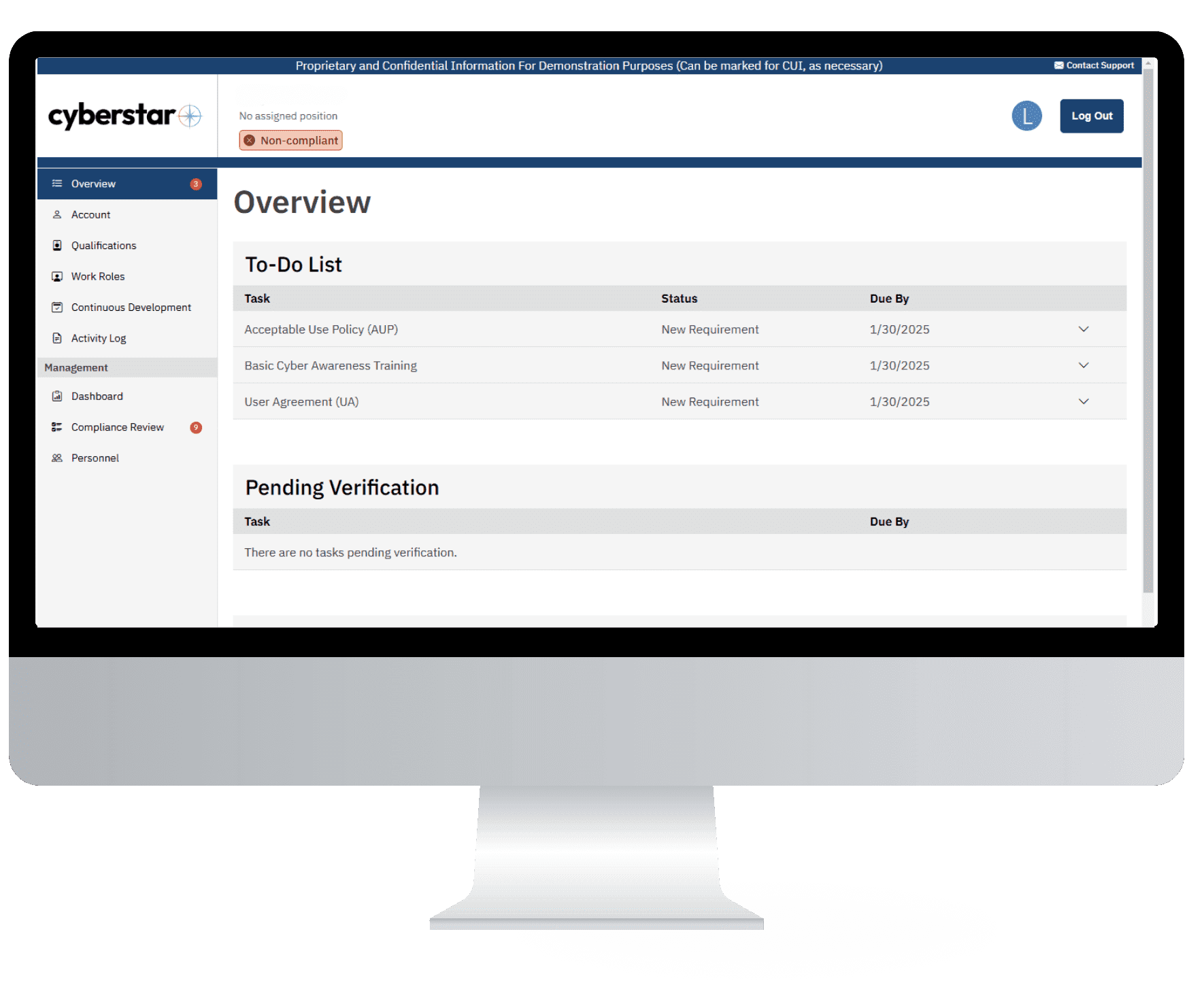
Real-Time Insights Offer an Actionable Path to Compliance
Access your entire team’s compliance status & track each member’s critical path to compliance instantly, on-demand, with notifications when status changes.

Intelligent Automation With Intuitive, Customizable Role Mapping
Automatic certification validation, dynamic role mapping, qualification & waiver tracking, with a clear path to compliance for both managers & team members.

Workforce-Wide Analytics & Individual Team Member Views In a Single System
Metrics dashboards & fully configurable reporting offer a unified view of cyber workforce readiness, and allow team members to be proactive in achieving compliance by uploading certifications & requesting waivers.
Seamless Integrations With DoD Systems & Out-of-the-Box Support for the Latest DoD Standards
Native DCWF compatibility and built-in CAC support, classified environment ready, and a seasoned, U.S.-based onboarding & support team.
%
Demonstrated Reduction in Manual Tasks for Training & Compliance
Years of On-Time & On-Budget Service in Partnership with Agencies
Million Registered Users
%
DoD Personnel Using Our System
Cyberstar Blog
From Normandy to Network Defense: A Memorial Day Tribute Crossword Puzzle by Cyberstar
USSOCOM Selects Cyberstar to Modernize Cyber Workforce Management Under DCWF & 8140 Frameworks
Cyberstar has been awarded a significant multi-year contract with the United States Special Operations Command (USSOCOM) to implement our advanced cyber workforce management platform, strengthening defense capabilities through modern compliance solutions. View Press Release on PR Newswire A...
Cyberstar Named Premier Sponsor of DoD-CIO Cyber Workforce Summit in Washington DC
Cyberstar demonstrates industry leadership as premier sponsor of the upcoming DoD-CIO Cyber Workforce Summit in Washington DC, bringing advanced compliance solutions to the forefront of defense cyber discussions.
WillCo Tech CyberSTAR Rebrands as Cyberstar, Unifying Company Identity with Flagship Product
Long-standing defense cyber compliance leader WillCo Tech announces its complete transformation to Cyberstar, unifying the company name with its trusted flagship product while introducing a fresh brand identity and enhanced website.
Cyberstar: Now FedRAMP Fully Authorized
Cyberstar has achieved full FedRAMP authorization, enhancing its ability to deliver secure, zero-friction 8140 compliance solutions to defense cyber teams across classified and unclassified environments.
2025 DoD Cyber Readiness Report: Preparing Defense Teams for the Future of Compliance
As DoDD 8140 fully replaces the legacy 8570 framework, defense organizations face unprecedented compliance complexity amid evolving cyber threats and workforce mandates. This analysis explores how automation is becoming mission-critical for maintaining cyber readiness in 2025 and beyond.
Quantifying Compliance Automation: Introducing the Cyberstar Savings Calculator!
The Cyberstar Savings Calculator quantifies how our compliance automation platform transforms your federal cyber workforce operations. By analyzing your team structure, manual workload, and compliance requirements, we calculate the precise hours and budget you’ll reclaim annually. See exactly how Cyberstar eliminates administrative burden, streamlines compliance workflows, and delivers measurable ROI for DOD and federal security teams.
Integrating Cyber Readiness Into Core Operations: The 8140.03 Advantage
DoDD 8140.03 requires federal agencies to transform how they approach cyber workforce management. Discover how integrating cyber readiness into core operational strategies—through continuous qualification, role-specific competencies, and automated compliance—creates a more resilient organization capable of defending against sophisticated threats.
DoD 8140.03M: Timeline & Anatomy of Regulations
On February 15, 2023, the Department of Defense (DoD) released a new manual, 8140.03M, which provides guidelines for managing the DoD Cybersecurity Workforce (CSWF). The manual replaces the previous version, 8570.01-M. What is 8140.03M? What is 8140.03M? 8140.03M is the new manual that outlines...
Implementing Your 8140 Program Now: Strategic Advantages of Early Adoption
When to adopt the DoD’s 8140.03 directive has been a lingering topic of conversation across the DoD cyber workforce since it was announced. Implementing a purpose-built compliance system like Cyberstar now—ahead of compliance deadlines—transforms this challenge into a strategic advantage, providing clarity for personnel and comprehensive visibility for leadership.
DoD 8140 Advantages over 8570: Transforming Challenges into Opportunities for Modern Cyber Workforce Management
Despite its complexity, DoDD 8140.03 offers unprecedented opportunities to modernize federal cyber talent management. From multiple qualification pathways to precise role alignment, discover how the right implementation approach transforms compliance challenges into strategic workforce advantages.
The Complete Guide to DoD Cyber Workforce Framework (DCWF): Compliance, Roles, and Implementation
The DoD Cyber Workforce Framework (DCWF) standardizes cybersecurity roles across defense organizations, defining 54 work roles in 7 categories. This guide explains what the DCWF is, why it matters beyond compliance, and how to implement it effectively in your organization.
Next Steps
Let’s start the conversation about how Cyberstar can help your cyber workforce mission succeed.
Product: Intro Call
Meet with a Cyberstar Product Specialist
60 Min Demo & Q+A
Ready to Schedule a Cyberstar Product Demo?
Contact Cyberstar
Ready to transform how your DoD cyber team handles workforce compliance? Reach out to Cyberstar with this contact form and our defense-focused team will spring into action. You’ll be connected with a compliance specialist who understands the unique challenges of DoD 8140 requirements and can demonstrate how our platform eliminates the friction that’s been slowing your team down.
From your initial inquiry to implementation, we provide a clear, mission-ready path forward. Our team will assess your current compliance processes, identify optimization opportunities, and create a customized deployment plan that minimizes disruption while maximizing results. Whether you’re wrestling with certification tracking, role mapping, or DCWF integration, Cyberstar delivers the modern, intuitive solution that defense cyber teams trust.